Cyber security SEO helps attract potential clients at the exact moment they search for protection, compliance, or threat response. This gives you a chance to boost online visibility and attract high-intent buyers through targeted search queries.
To turn that visibility into real sales, you must combine a solid technical foundation, expert-driven content, and user trust. Maximizing conversions requires meeting Google’s standards while supporting long, research-heavy buying cycles. Let’s look into the factors that ensure effective SEO for cybersecurity companies – and how you can apply those insights in practice.
- High-intent queries drive stronger leads than passive marketing.
- Trust signals (HTTPS, privacy policies, author bios, etc.) impact search engine rankings.
- Topical authority relies on expert-led, technically accurate content.
- Full-funnel content is essential for lengthy, complex cybersecurity sales cycles.
- Backlinks from trusted sources increase credibility and search visibility.
Why SEO Matters in the Cybersecurity Industry
While SEO connects you with buyers who are actively evaluating cyber security solutions, visibility alone isn’t enough. You must also demonstrate trustworthiness, authority, and relevance from the very first search. Below is a look at how search intent and trust signals shape effective SEO strategies for your cyber security brand.
High-Intent Leads from Search
When people actively seek cybersecurity solutions, they turn to Google with a clear objective. These search engine users type in problem-driven, long-tail keywords, like “best MDR providers for healthcare” or “SOC 2 compliance checklist.”
By targeting these search terms, you position your company in front of prospects who are already in the market for your security solutions. Relevant keywords often reflect pain points or readiness to buy, attracting users who are much more likely to convert than those reached through passive channels.
Analyze competitor pages’ ranking for cybersecurity SEO keywords using tools like Ahrefs. Identify content gaps or weak CTAs, then create more actionable pages to outrank them and capture ready-to-convert traffic.
Trust Signals and Their Impact on Search Engine Rankings
Potential clients need immediate evidence that your company understands complex threats and operates with authority. That evidence comes from trust signals, which influence both human perception and Google’s search algorithms.
These signals include visible indicators like detailed author bios, third-party certifications, client testimonials, case studies, transparent company information, and more. At the same time, they align with Google’s E-E-A-T framework (Experience, Expertise, Authoritativeness, Trustworthiness), which plays a critical role in SEO rankings. Especially for new businesses, E-E-A-T is important at an early stage, since your domain isn’t strong yet and every trust signal must be built from scratch.
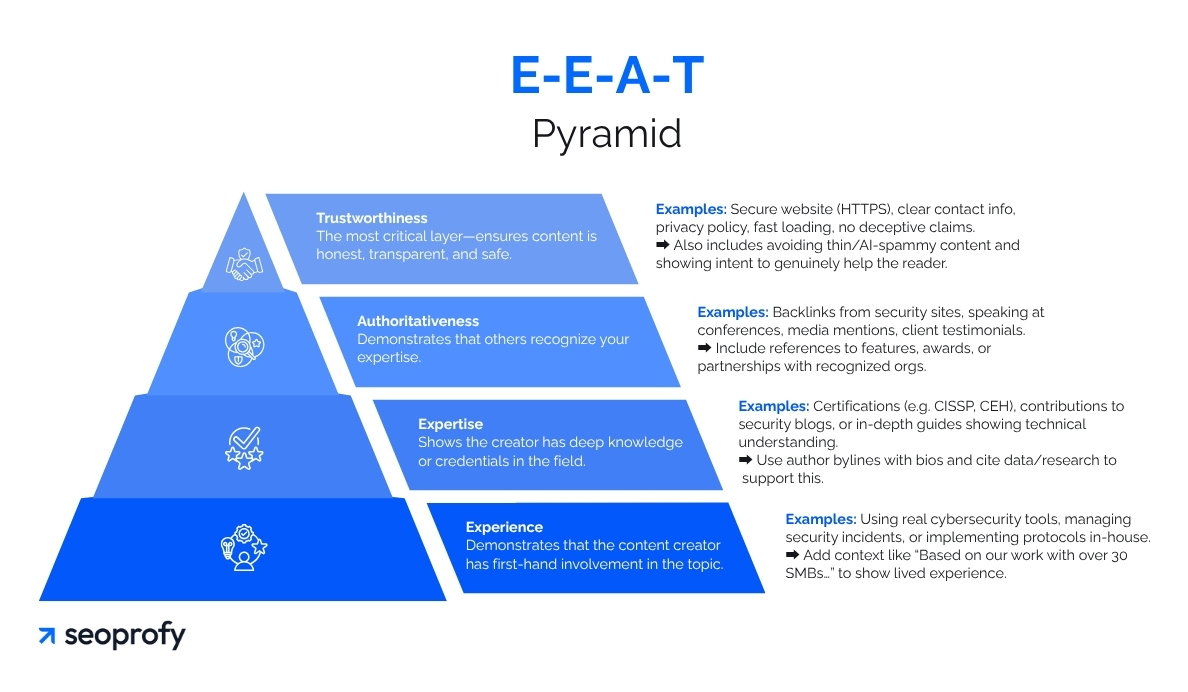
You can reinforce these signals through high-quality, educational content that addresses specific concerns, such as ransomware mitigation, compliance mandates, or threat intelligence. When Google sees that your content demonstrates deep knowledge and satisfies search intent, your pages are more likely to rank.
By establishing company transparency and creating helpful, reliable, people-first content, you reassure your prospects and send strong ranking cues to Google.
How Cybersecurity Impacts SEO (and Vice Versa)
Cyber security isn’t just critical for protecting users. It also affects how your site performs in search. Let’s outline how security measures influence your rankings and how to avoid common risks that can undermine your SEO efforts.
Google Prefers Secure Websites
Like any other search engine, Google favors secure websites. For example, HTTPS, enabled via an SSL certificate, encrypts user data in transit and signals to Google that your domain meets baseline security standards. If you implement HTTPS on your site, you demonstrate a commitment to protecting users.
But it’s not just about encryption. If your site is compromised through malware, phishing, defacement, or deceptive redirects, the SEO damage can be severe. Google may blacklist the domain, strip it from search engine results pages, and flag it in browsers — cutting off organic traffic. The recovery process is often long and difficult.
These breaches also affect off-page metrics: Referring domains often remove backlinks to avoid association with a risky site.
Run regular malware scans and set up Google Search Console alerts so you can catch security issues early — before they damage your rankings or get your domain blacklisted.
Trust Signals = SEO Signals
Google’s trust signals further include clean backlink profiles and transparent on-site policies. All these elements tell the search engine that your domain is legitimate and user-safe. They also shape user behavior: Without them, visitors often distrust the site and exit immediately.
Additionally, warnings, like Not Secure browser labels, reduce click-through and increase bounce rates. This signals to Google that your site may not satisfy user intent, leading to a drop in SEO rankings.
SEO Challenges for Cybersecurity Companies
Search visibility in cyber security depends on more than keyword targeting. In addition, brands must navigate Google’s quality standards and the complex nature of cyber security purchasing decisions. Explore the key challenges affecting SEO performance in the industry and what it takes to compete.
E-E-A-T & YMYL Impact on Cybersecurity SEO
One of the biggest challenges for cyber security SEO is Google’s strict quality standards under the E-E-A-T framework we mentioned earlier. Content in this industry often falls under the YMYL (Your Money or Your Life) category. This means it’s likely to impact users’ financial stability, privacy, or safety. As a result, Google applies heightened scrutiny to cybersecurity websites, since inaccurate or misleading advice can lead to serious harm, such as data breaches or financial loss.
Consequently, it’s not enough to publish regularly or rely on basic search engine optimization tactics. A detailed SEO audit is essential to check that your domain is secure and your content is created or reviewed by subject matter experts. If you don’t meet these benchmarks, even well-written content will be at a disadvantage in search rankings.
Funnel-Wide SEO Content for Long Sales Cycles
Cyber security purchases are rarely quick. Complex solutions, high stakes, and multi-layered approvals make for long, research-intensive sales cycles.
However, many cyber security companies struggle to align their SEO strategies with how their buyers actually make decisions. As a result, they over-focus on bottom-of-funnel (BOFU) keywords like “best XDR software” or “top penetration testing tools”, while neglecting the early and mid-stage needs of buyers.
This creates gaps in visibility and trust during the awareness and consideration phases, when prospects begin shaping their vendor shortlist. To tackle this challenge, SEO content must address every stage of the buyer’s journey – from initial problem recognition to vendor evaluation.
To avoid visibility gaps, you need a strategy that combines expert content with full-funnel SEO, all aligned with Google’s guidelines and algorithm updates. Book a consultation and get the following:
- Fix technical SEO and meet E-E-A-T standards
- Rank for cyber security keywords that drive real leads
- Earn trusted backlinks without risking penalties

Proven Strategies for Cybersecurity SEO
In a competitive cyber security market, your SEO strategy must go beyond surface-level tactics. Below, learn how to arrange technical optimization, authoritative content, and ethical link building to increase visibility, earn trust, and support long-term growth.
Technical SEO and Site Security Working Together
As you already know, Google prioritizes user safety. For this reason, website security has become a foundational component of technical SEO, not just a backend concern.
HTTPS and SSL: Secure Data Transmission
Earlier, we mentioned that SSL certificates enable HTTPS, which encrypts data between browsers and servers. This builds trust with users and supports rankings by lowering bounce rates.
To ensure full protection, HTTPS should be enabled on all URLs. Enforce HSTS (HTTP Strict Transport Security) and redirect all HTTP traffic to HTTPS through your server or CMS settings.
Security Headers: Defense Against Common Cyber Threats
Headers such as HSTS, X-XSS-Protection (Cross-Site Scripting Protection), and X-Content-Type-Options prevent known exploits. These controls improve safety and help maintain search visibility. Apply them through server configuration files or your content management system to harden your site against common attack vectors.
WAFs and CDNs for Stability and Speed
WAFs (Web Application Firewalls) block malicious traffic before it reaches your site. CDNs (Content Delivery Networks) improve load times and absorb traffic surges, which helps preserve crawlability and user experience.
To improve both speed and resilience, implement a CDN with built-in DDoS (Distributed Denial of Service) mitigation and connect it to a cloud-based WAF.
Using Indexation Controls to Hide Sensitive Content
Google relies on robots.txt and XML sitemaps to guide crawling. Incorrect settings may expose private areas or waste crawl resources.
Block non-public sections and submit accurate sitemaps through Google Search Console so crawlers can navigate your website more efficiently.
CAPTCHA and Bot Filters for Protecting Interactive Features
CAPTCHA stops bots from abusing forms. This reduces risk and avoids penalties related to spam or brute-force attacks. Make the most of this security measure by placing CAPTCHA on all forms, especially those tied to trials, logins, or gated assets.
Compliance with Privacy Laws
Non-compliance with laws such as GDPR (General Data Protection Regulation) or CCPA (California Consumer Privacy Act) can trigger fines and damage trust. Poor data practices also lead to negative engagement signals.
To establish trustworthiness with both users and Google, you need to leverage consent tools, manage data access responsibly, and publish transparent privacy policies.
Strong security measures – HTTPS, headers, WAFs, CDNs, crawl directives, and legal compliance – all enhance technical SEO, keyword rankings, and trust.
Creating Expert-Led, Authoritative Content to Build Topical Authority
Topical authority allows you to rank for competitive terms and earn trust from technically savvy audiences. This authority builds up when Google detects consistent, high-quality content focused on a specific cyber security subject, especially when written or reviewed by recognized technical professionals.
Such content prompts the search engine to begin associating the domain with that subject area. As a result, keyword rankings improve for both broad and niche cybersecurity search terms, and visibility grows in features like People Also Ask.
Amid today’s AI-driven landscape, unique content entities, such as expert-led topic clusters, deliver strategic value. They help Google connect your brand to specific subjects and strengthen authority across semantic search features.
Here’s what content you need to enhance topical authority:
- Blog posts by security experts: Focus on real-world cyber threats, vulnerabilities, and security solutions. Ensure authors have verified credentials.
- Whitepapers and thought leadership: Explore complex issues like GDPR, CCPA, or zero-day threats in depth.
- Webinars and videos: Share valuable insights from security architects or response teams to improve engagement and build credibility.
- Infographics and explainers: Clarify technical concepts like encryption or threat intelligence using visual formats.
- Evergreen guides: Maintain long-term resources on security best practices and compliance. These pages attract high-quality backlinks and support internal linking.
Google rewards expert-authored content with better search rankings, more visibility in features like People Also Ask, and higher trust signals from users. This approach turns your cyber security content into a strategic SEO asset.
Link Building & PR: Earn Mentions in Reputable Cyber Channels
In cyber security, where trust drives buying decisions, backlinks from respected media outlets, technical blogs, and expert communities serve as public endorsements. Links from platforms like Dark Reading, CSO Online, or Cybercrime Magazine strengthen your cyber security SEO, signal authority to Google, and legitimize your brand in the market.
To earn these links while staying within Google’s guidelines, use ethical, content-driven tactics:
- Guest contributions on cyber security platforms: Submit expert articles to leading blogs and publications. This positions your brand among peers while earning editorial links embedded in the content, not buried in bios or footers.
- Original research and technical reports: Publish threat intelligence studies, compliance surveys, or case-based whitepapers. Unique, data-backed insights attract citations from analysts, bloggers, and media sources.
- Influencer and research collaborations: Co-author content with security researchers or known experts. Their reputation can lend weight to the content and earn natural backlinks from engaged audiences.
- Digital PR via HARO, SOS, and Qwoted: Offer technical commentary to journalists covering cyber security. When used strategically, these platforms yield mentions in news outlets and trade publications, often with high-quality backlinks.
- LinkedIn and forum engagement: Share research and analysis in targeted LinkedIn groups or forums like Reddit r/netsec and StackExchange Security. Technical readers often link back to well-argued posts or insights when referencing them in blogs or newsletters.
Enhance your backlink profile by anchoring it in a strong internal and external link structure. Internally, verify that your cyber security assets link logically – for example, a blog on threat detection should connect to a relevant case study or solution page. Externally, cite credible references like NIST or MITRE ATT&CK. This reinforces your content’s trustworthiness.
When assessing backlinks, prioritize links from domains with high authority, topical relevance, and contextual placement within the main content. Use clear, descriptive anchor text and avoid keyword stuffing or exact-match spam. Editorial placement matters as well – links embedded in well-written content carry more weight than those in comments or footers.
Don’t believe myths and stay away from paid link schemes, link farms, or generic directories, as these can lead to penalties and erode trust. If you use an agency, vet them carefully. Partner only with those who ensure placements in recognized cyber security outlets, not random SEO blogs.
Real Case Study: How SEO Grew a Cybersecurity Firm’s Traffic
To show how cybersecurity SEO works in practice, let’s review the case of Check Point, a leading market player. The niche is broad, but the competition is fierce – yet the company achieved major gains in organic traffic and authority worldwide by building a structured content framework.
SEO Strategy Overview
First, Check Point’s SEO growth was driven by a well-organized site structure. Second, the team didn’t only focus on commercial pages but also delivered supporting content to demonstrate topical authority. Informational pages covering emerging threats, best practices, and industry trends worked to fit into Google’s E-E-A-T framework. They didn’t directly sell but established credibility, attracted links, and drew visitors searching for guidance.
Results
The numbers speak for themselves. Check Point saw the following wins:
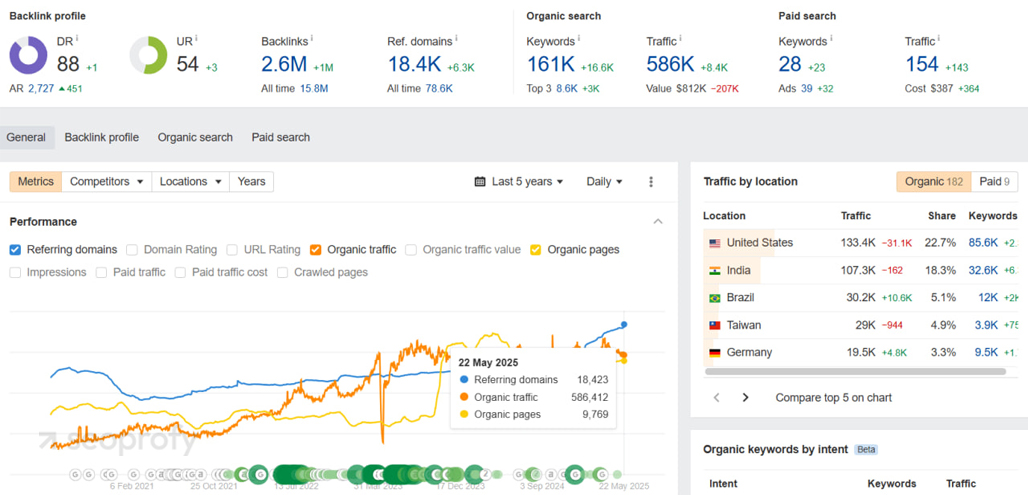
- Massive organic traffic growth: Organic traffic reached 586K monthly visits, up by 8.4K recently. This reflects strong, consistent performance across many pages.
- Keyword expansion: The site ranks for 161K organic keywords, a growth of 16.6 K. Out of these, 8.6K are in the top 3 positions.
- Backlink and authority surge: With 2.6M backlinks (+1M) and 18.4K referring domains (+6.3K), the site has become a magnet for inbound links, a clear sign that the content resonates across the industry. The domain rating is now 88.
- Global reach: While the United States remains the top traffic source (133K), there’s traction in India (107K), Brazil (30K), Taiwan (29K), and Germany (19.5K). This signals successful international SEO execution.
Conclusion
SEO gives cyber security brands a direct line to high-intent buyers, but only if it’s done right. Note that Google demands expertise, strong security, and credible content. That means you need a secure site, expert-led pages, and a strategy that supports the full sales cycle, from early research to final decisions. When backed by real authority and clean technical execution, cyber security SEO drives consistent leads, builds trust, and strengthens your market position.